
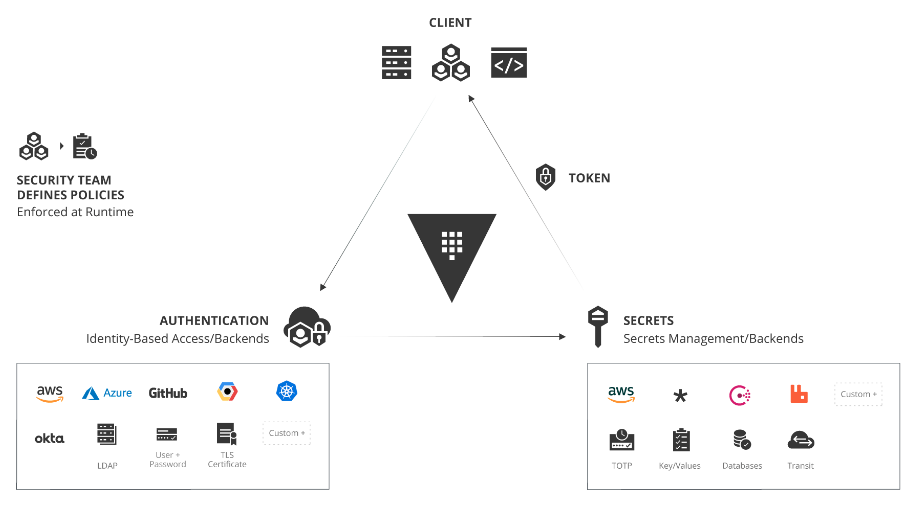
Vault protects, stores, and controls access to passwords, certificates, encryption keys, and other sensitive data in a dynamic infrastructure. Its security model is based on the principles of access identity and security protection, and any user or machine must be authenticated to define what they can do.
100+
integrations
10,000+
daily unique tokens generated
90%
less time spent on secrets management
Why Vault
Reduce the risk of data exposure
Encrypt sensitive data with Vault's centralized management and encryption keys through a single workflow and API
Reduce the risk of vulnerability attacks
Centralize confidential information in Vault and control access with identity-based standards
Improve Productivity
Enables development teams to automatically use confidentiality in application delivery and protect sensitive data programmatically through a single API, increasing productivity with consistent workflows and encryption standards
How Vault works
1
Adopt -
Adopt centralized secrets management to eliminate secret sprawl across.
2
Build -
Build out enterprise supported secrets management to automate application delivery and consume secrets programmatically.
3
Standardize -
Standardize Vault as a service with encryption workloads.
4
Innovative -
Innovate with advanced data protection workloads to protect even the most sensitive data.
Vault 的使用場景
Secrets management
- Vault Secret Engines
Secure access to certificates, keys and other types of secrets without the need to deploy complex systems - Dynamic secrets
Vault gives dynamic tokens (not certificates) to guarantee access security
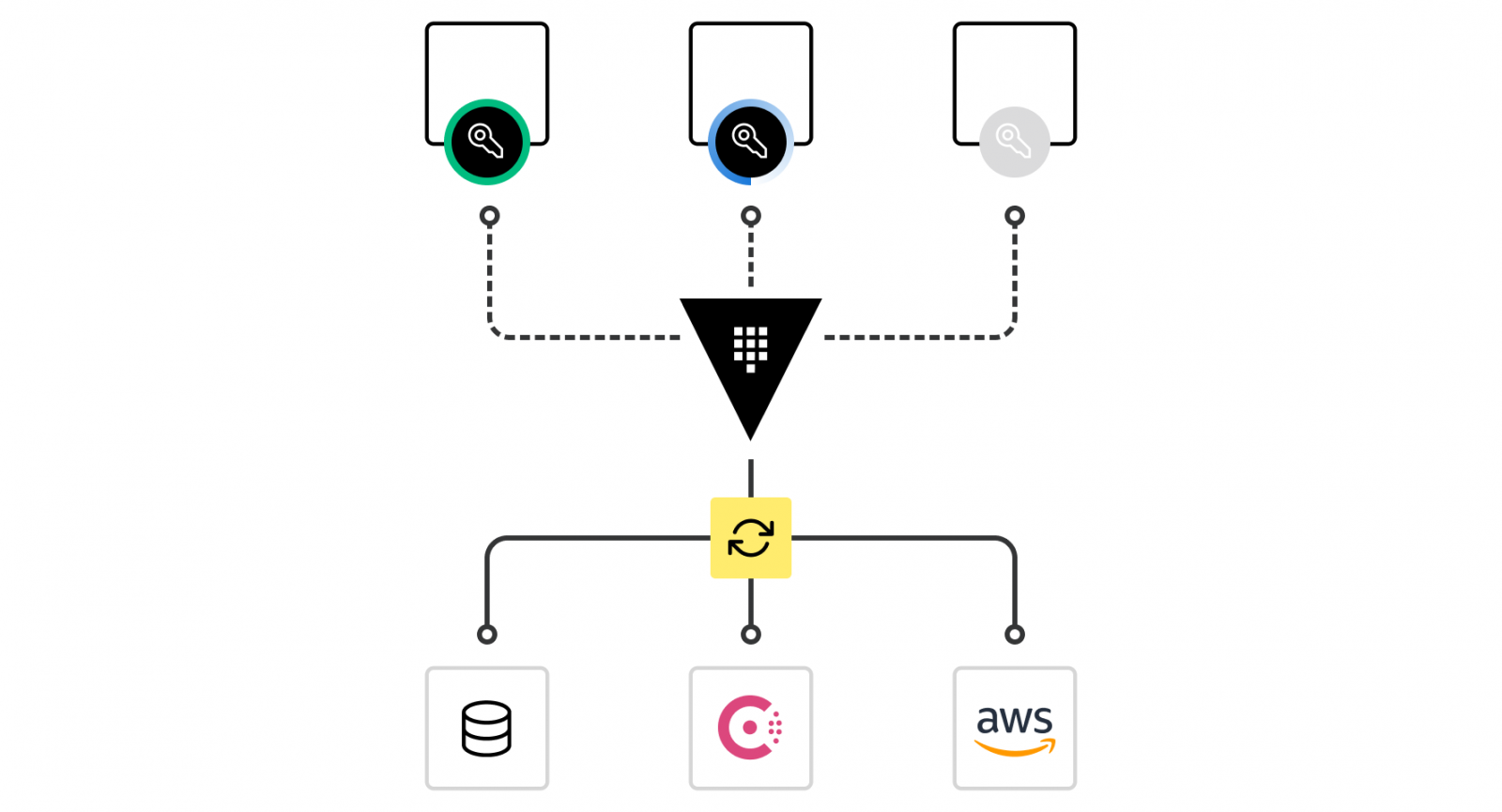
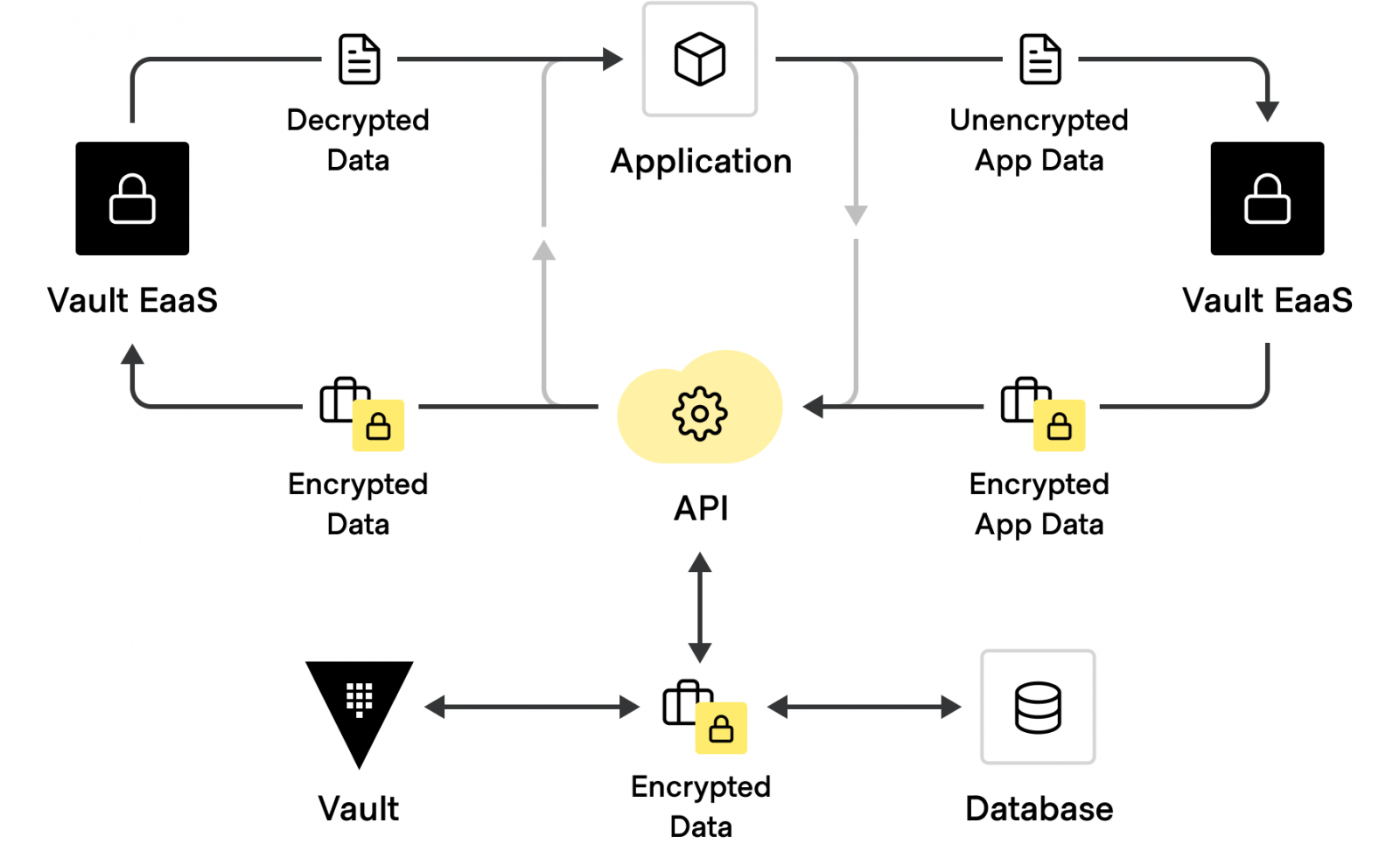
Encrypting application data
Secure application data with centralized key management and APIs for encrypting/decrypting data
- API-driven encryption
Uses Transit encryption engine to handle encryption, decryption of application data and encrypted signatures, allowing users and applications to perform encryption workloads without a key management infrastructure - Encryption key rolling
Updates and rolls keys in a distributed infrastructure while retaining the ability to decrypt encrypted data
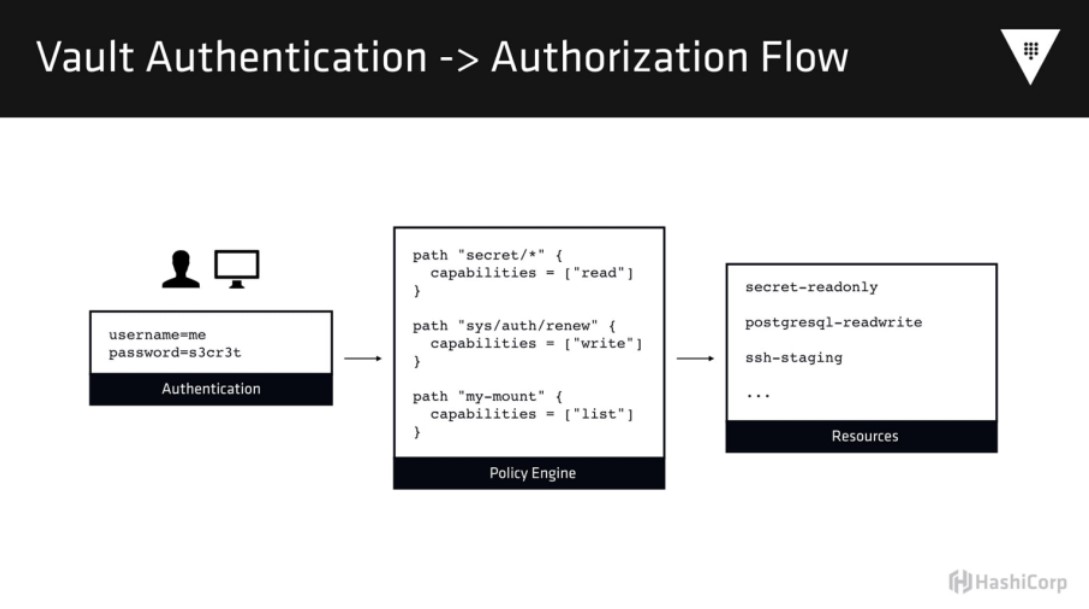
Access Control
- Control RBAC of multiple certificates and applications with a single line of code through ACL
- Use Sentinel policy to further require users to connect or access specific secrets through specified authentication methods


