Using GitLab CI/CD to deploy Ingress Controller and Cert-Manager
Level: Beginner
Data: Mar 11 2021
Edited by: Webber Lin
Goal
Leveraging Gitlab CI/CD managed-apps to simplify the management of K8S infrastructure implementation is a "must-try" method if you are new to Kubernetes and GitLab. You don't need to handle complicate installations on these basic infrastructure by yourself because GitLab managed-apps can help you out. In this document, we would like to demonstrate you how to implement ingress controller and cert-manager to serve HTTPS/TLS web services.
GitLab provides GitLab Managed Apps for various applications which can be added directly to your configured cluster. These applications are needed for Review Apps and deployments when using Auto DevOps. You can install them after you create a cluster. GitLab provides GitLab Managed Apps using CI/CD. GitLab Managed Apps with one-click installations have been deprecated, and are scheduled for removal in GitLab 14.0. https://docs.gitlab.com/ee/user/clusters/applications.html#install-ingress-using-gitlab-cicd
Before you start this implementation, you need to prepare your own accounts as below:
Prerequisite
- GitLab Account
- GCP Account (either one)
- AWS Account (either one)
Let's start!
- Create a new project from template
- Add a K8S cluster (GKE)
- Add a K8S cluster (EKS) - update soon
- Configure Ingress Controller and Cert-Manager installation
- Verify your installation
Create a new project from template
- go to your gitlab project page to create a new project - https://gitlab.com/projects/new
- choose "create from template - https://gitlab.com/projects/new#createfromtemplate
- click on the "Use template" button of GitLab Cluster Manager
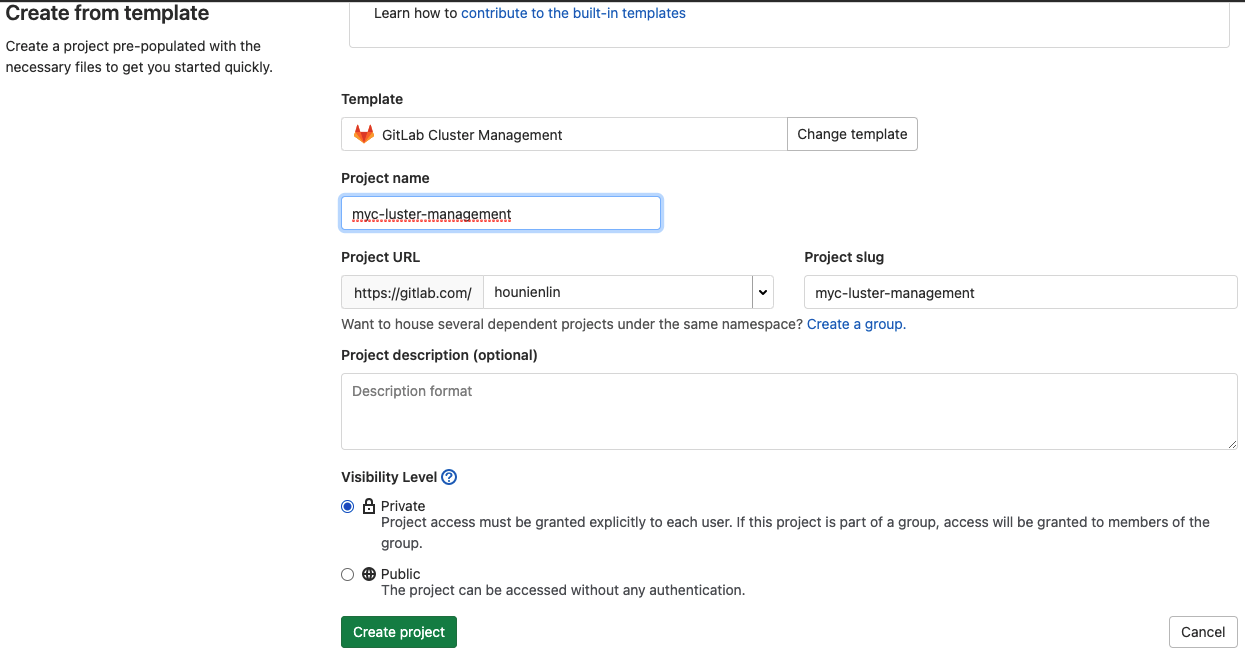
- provide necessary information for this project - project name, project description, visibility level then click on the Create project button.
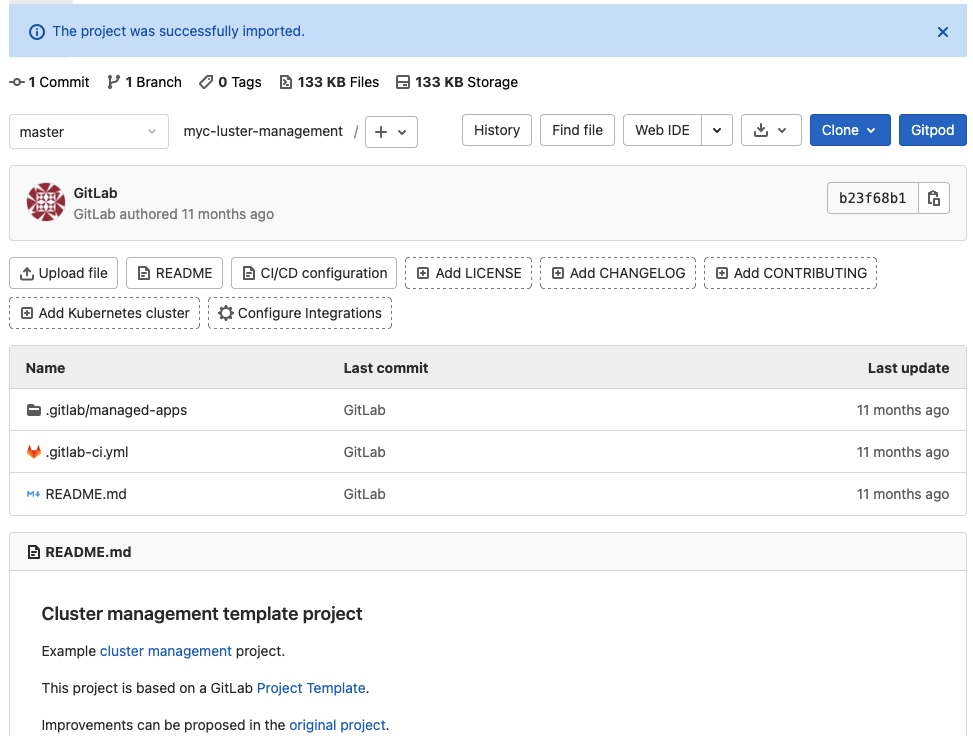
- GitLab redirects you to the project overview page and you will see below
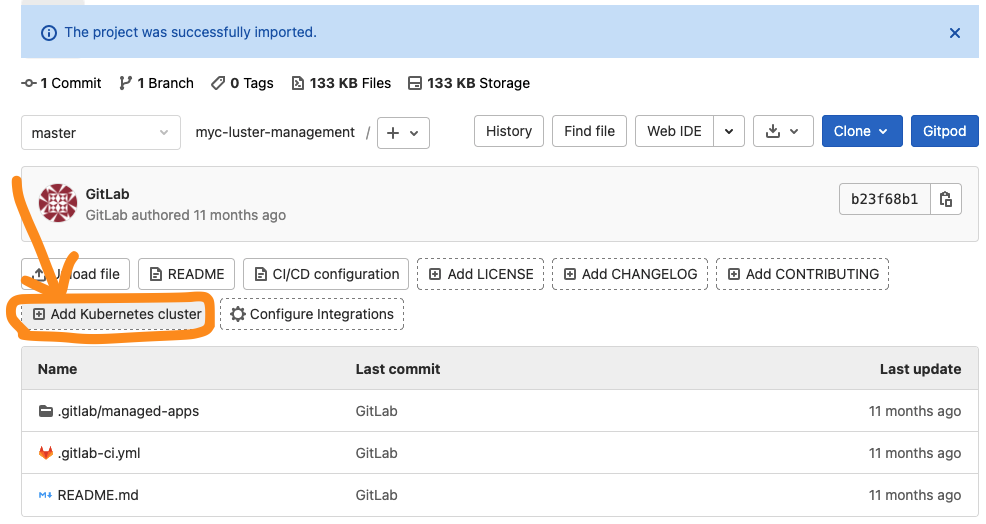
- Now you are all set and ready to move to the next step.
Add a K8S cluster (GKE)
- click on the add kubernetes cluster
- create a new cluster and choose GKE

- it rediects you to Google SignIn page and choose the one GCP enabled
- configure the cluster with kubernetes cluster name, google cloud platform project, zone, and machine type. You can keep default value for other fields.
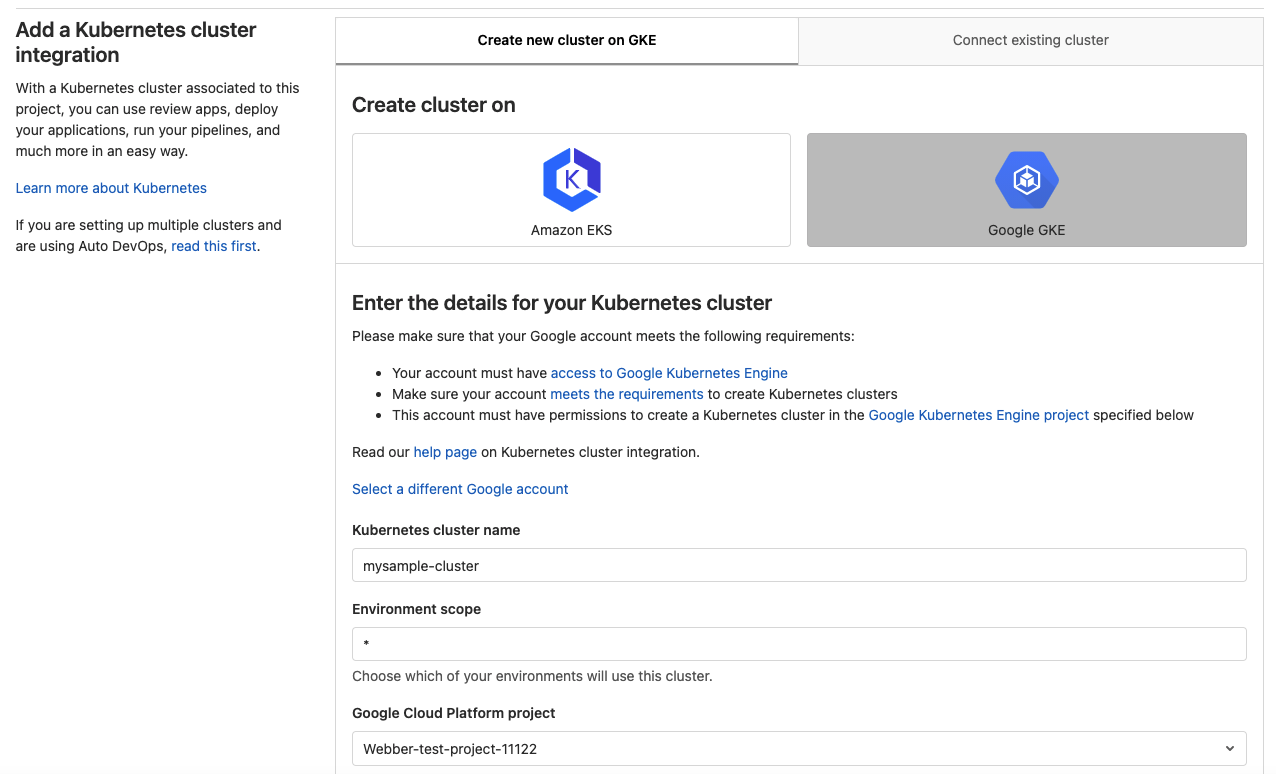
- click on create kubernetes cluster
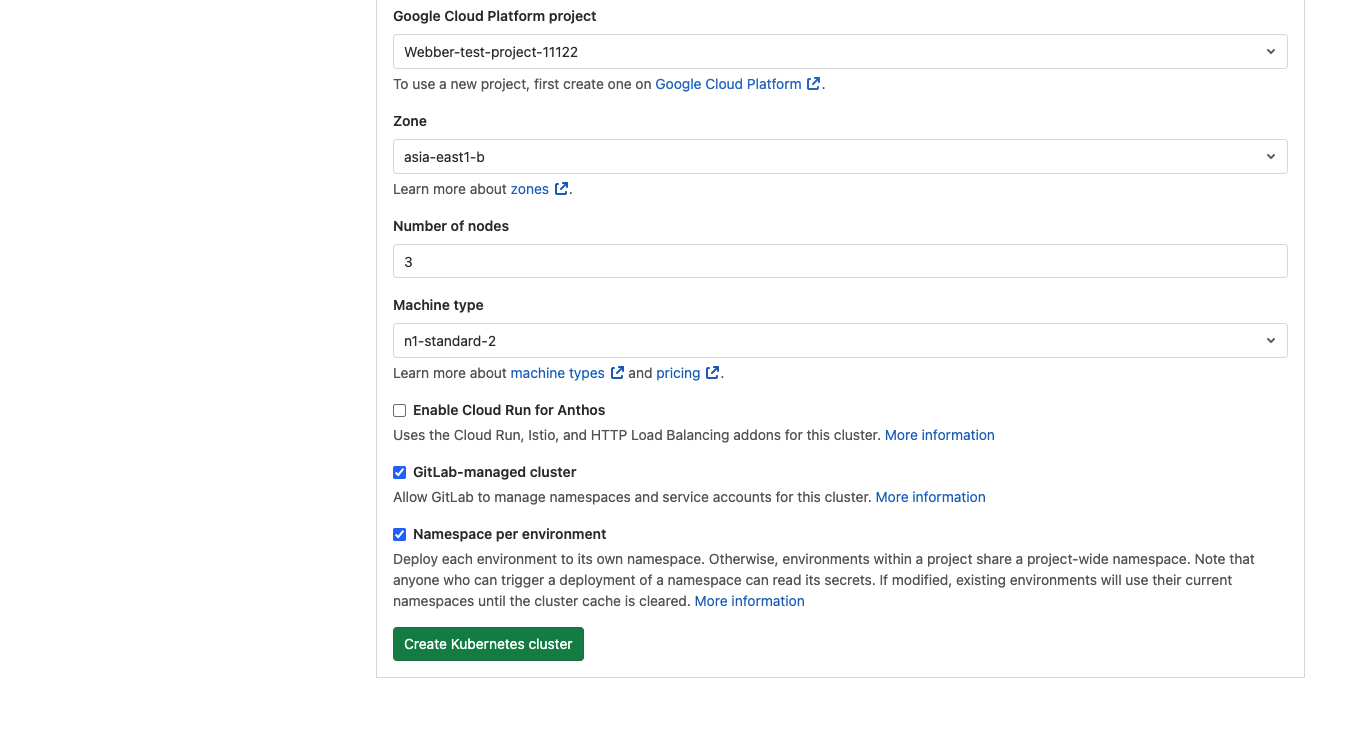
- it might take up to 10 minutes for bringing up a K8S cluster. (enjoy a cup of tea!)
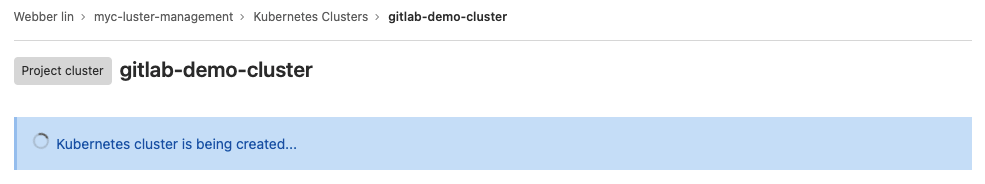
- If you see below, it means your K8S cluster is ready.
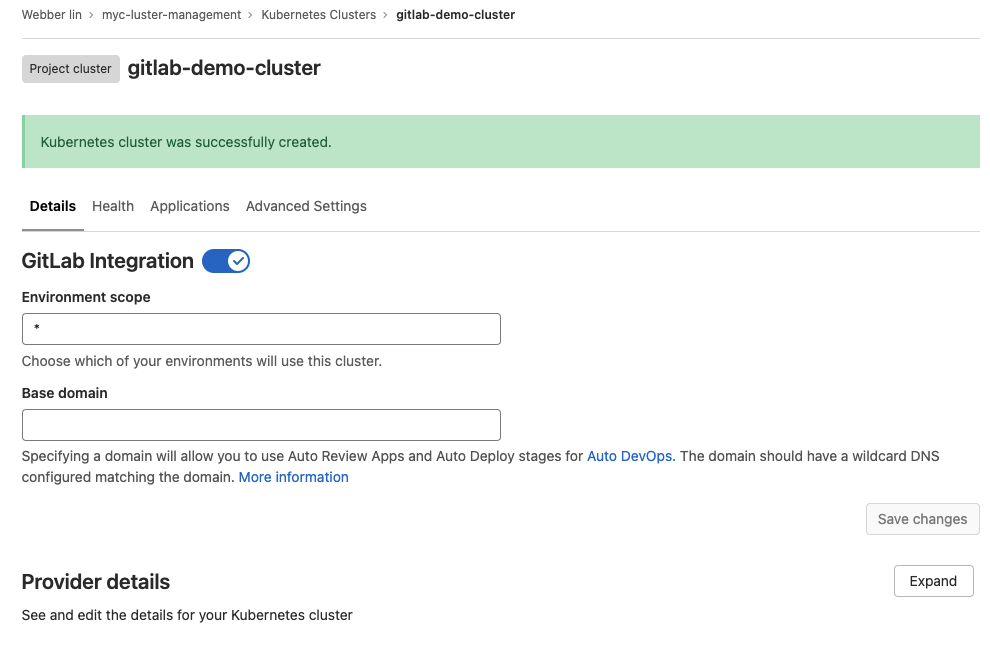
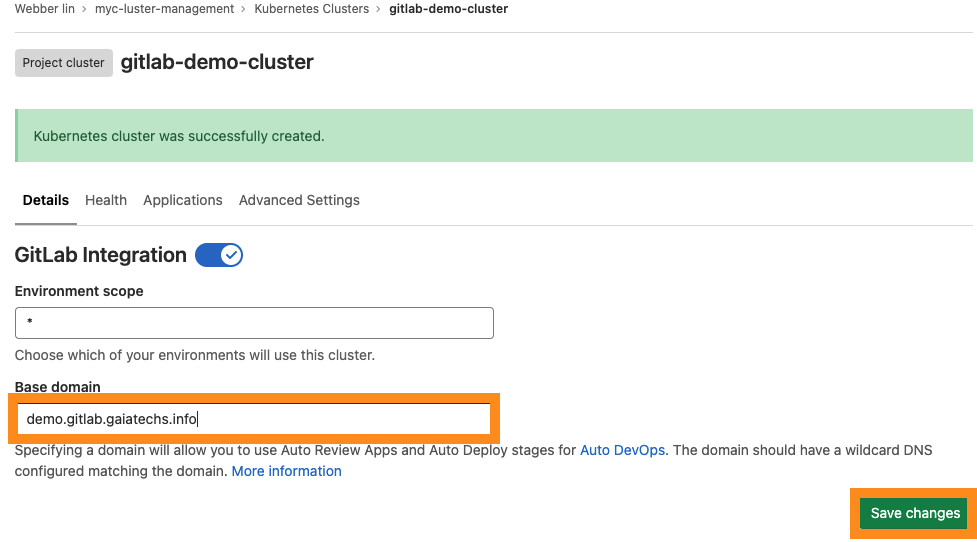
- In the details tab (default tab), edit your base domain for later DNS configuration.
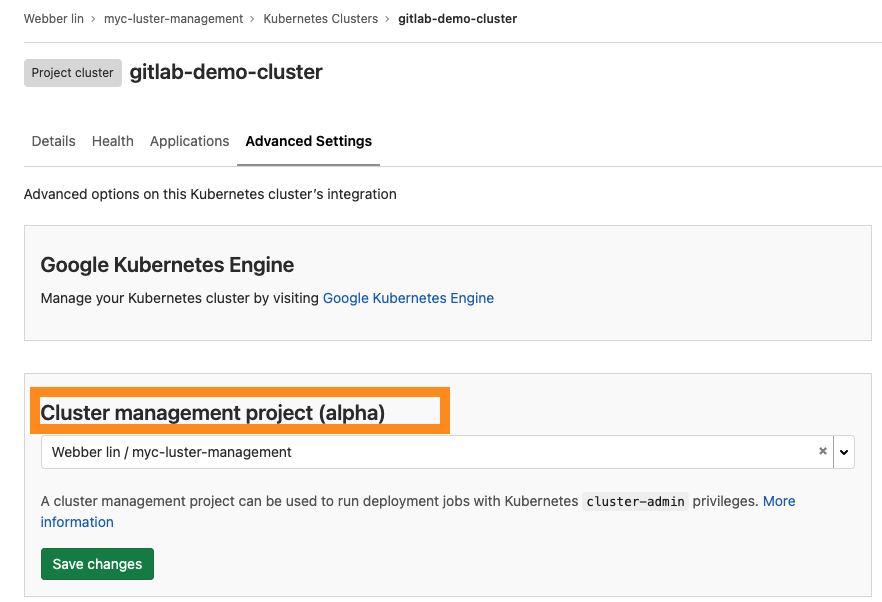
- Click on the "Advance Settings" tab and enable your cluster management project. Choose your project from the drop-down box and click on the Save changes button. This step is to allow gitlab to have K8S cluster-admin previlleges for deployment.
- Now you are all set and ready to move to the next step.
Note: you might notice that my figures using different project name or cluster name because I forgot to take snapshots. Please forgive my mistakes. :-)
Configure Ingress Controller and Cert-Manager installation
Now we are going to edit some files to enable the installations of ingress controller and cert-manager.
You have to edit files under .gitlab/managed-apps
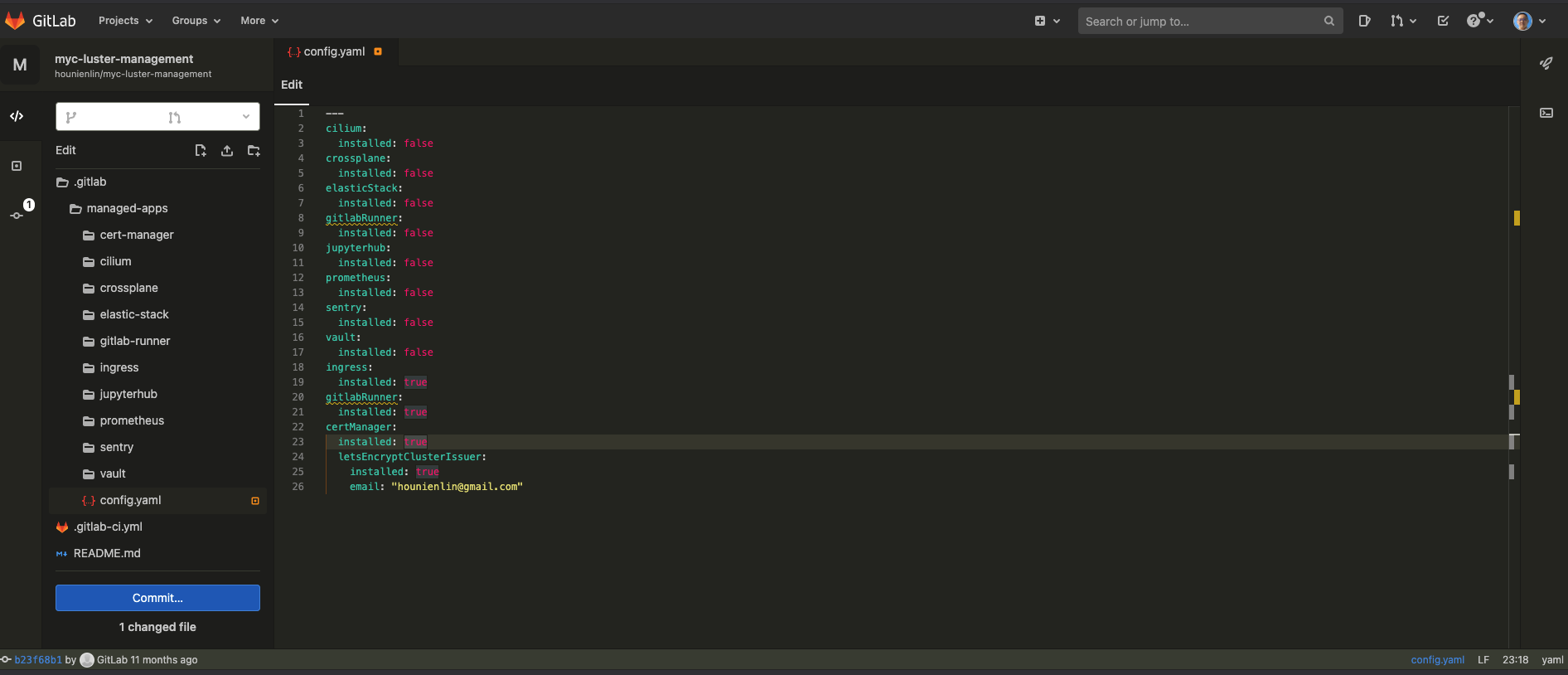
- config.yaml - change the installed value to "true" and add your email for certManager
cilium:
installed: false
crossplane:
installed: false
elasticStack:
installed: false
gitlabRunner:
installed: false
jupyterhub:
installed: false
prometheus:
installed: false
sentry:
installed: false
vault:
installed: false
ingress:
installed: true
gitlabRunner:
installed: false
certManager:
installed: true
letsEncryptClusterIssuer:
installed: true
email: "YOUR EMAIL@EMAILSERVICE"
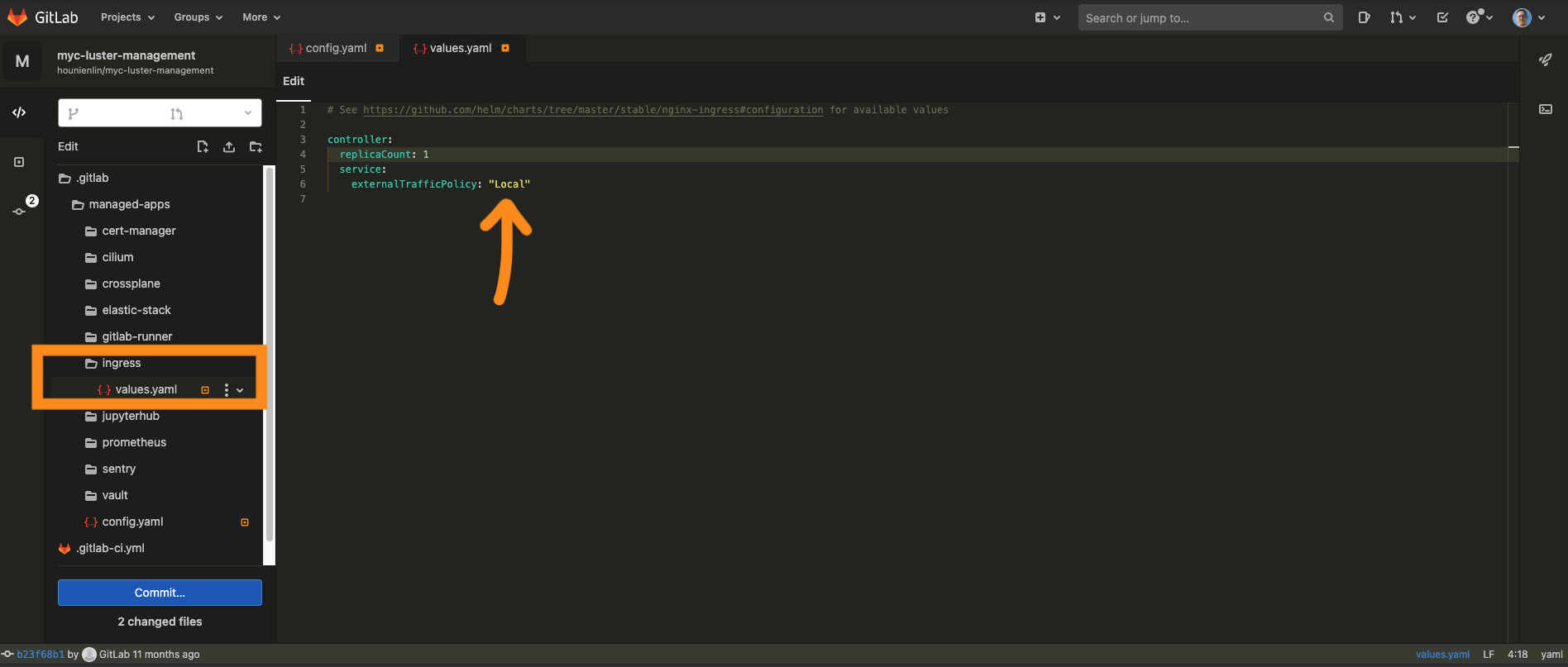
- ingress/values.yaml(optional) - the service I add here is for receiving end user's source IP (public IP) for later lab use.
replicaCount: 1
service:
externalTrafficPolicy: "Local"
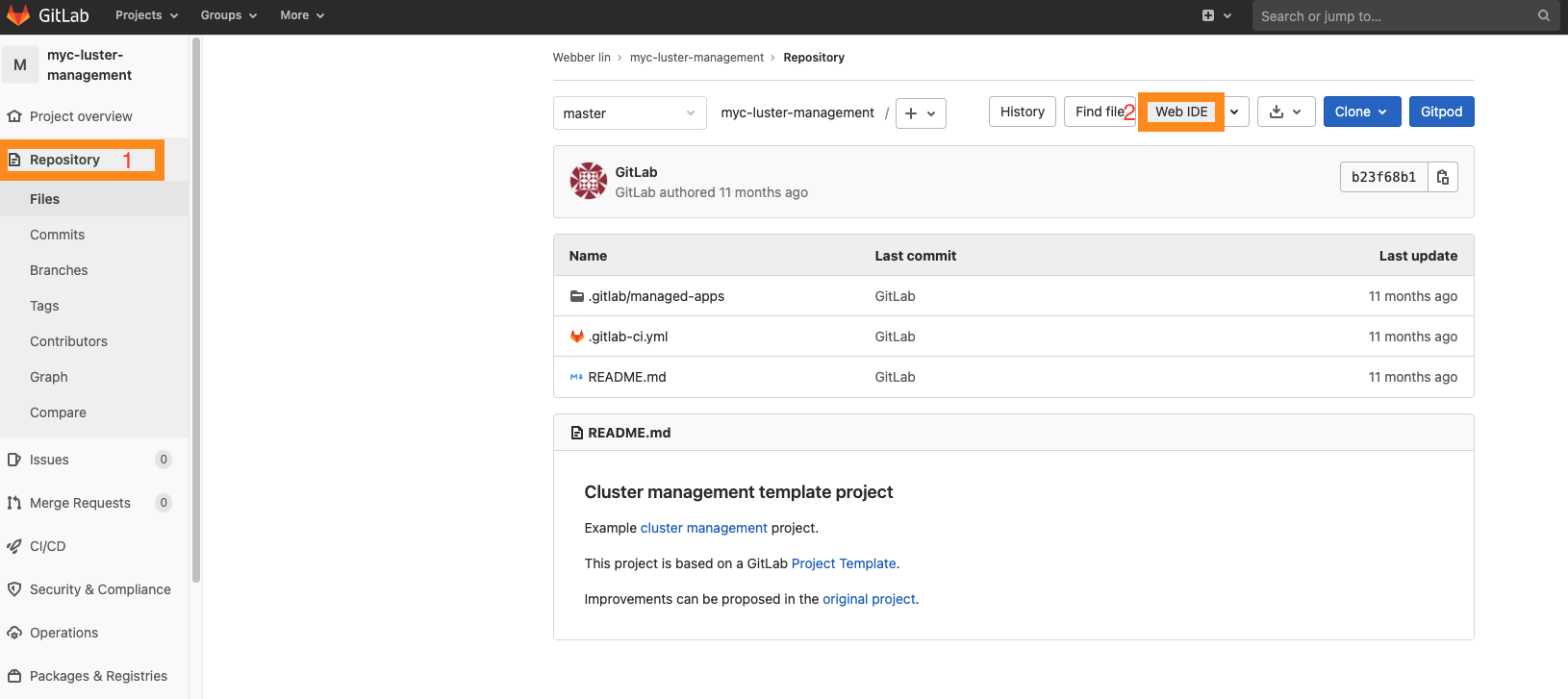
- click on the Repository of the side bar then click on the WebIDE
- In the GitLab WebIDE page, edit config.yaml file as below. You have to provide your email address for applying Letsencrypt issuer.
- Edit .gitlab/managed-apps/ingress/values.yaml file as below.
- click on the Commit button. Write your commit message and choose to commit to master branch.
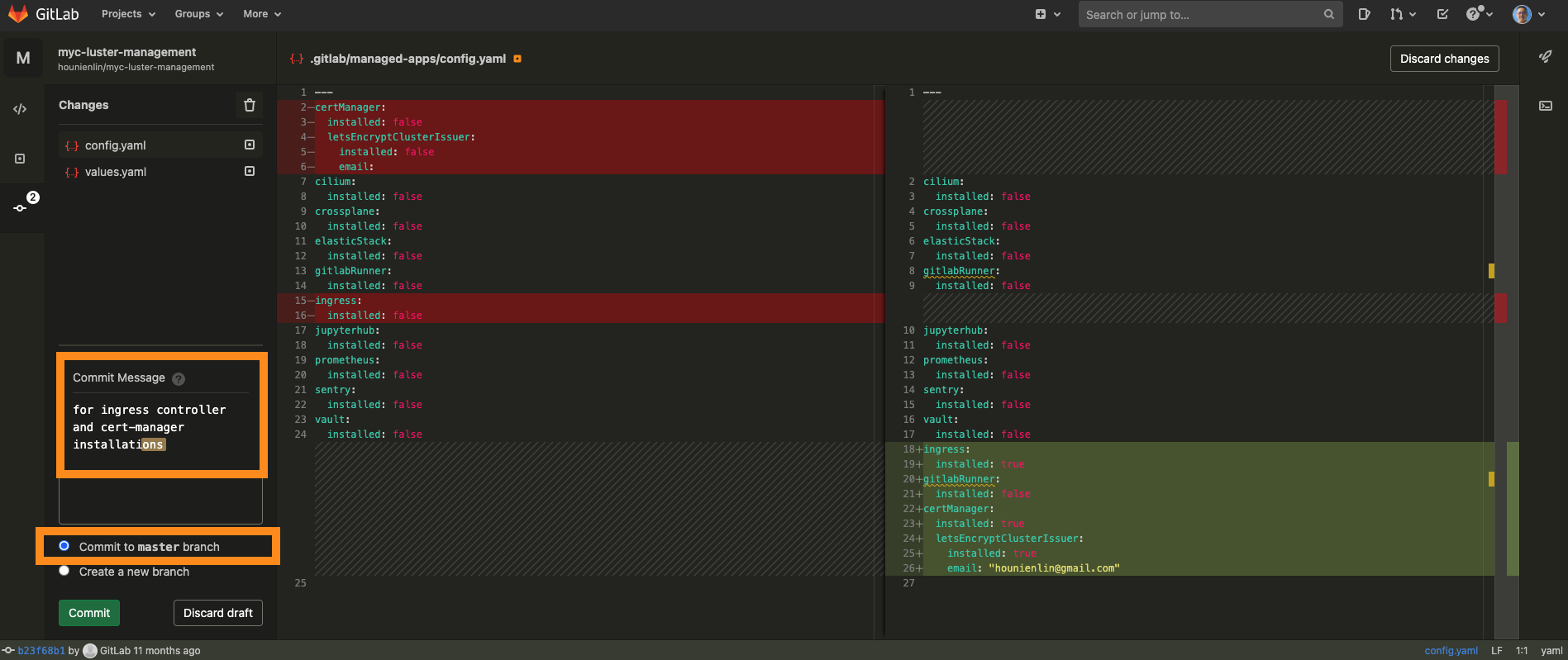
- click on commit
- Your CI/CD job is been scheduled by GitLab and let's move back to GitLab Project page. It might take 2-3 minutes for scheduling CI/CD jobs. You might see the job status is pending. Be calm!
- You can check the status as below - click on the CI/CD - jobs of sidebar as below
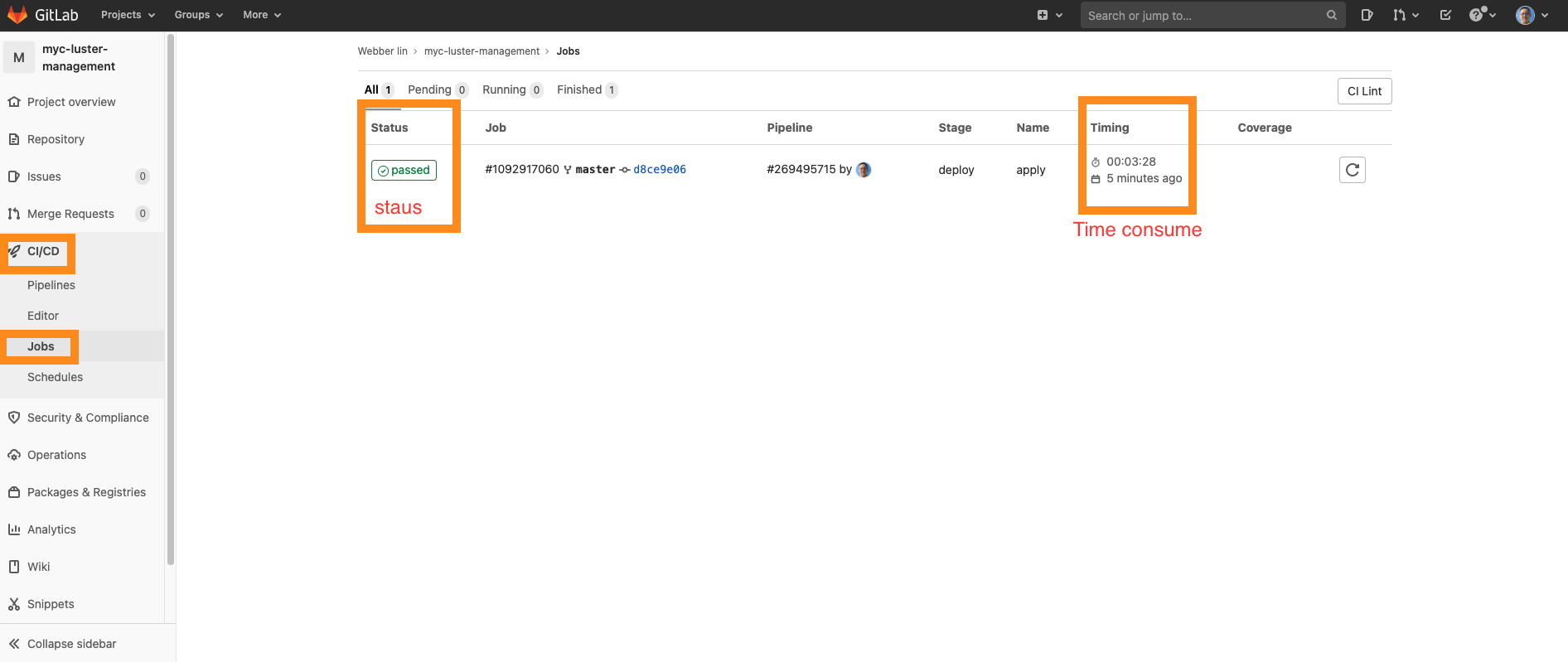
- Usually the job needs 3-5 minutes to be completed.
- If you also see "passed", you are all set and ready to move to the next step.
If you would like to gather some more details, you can click on the job status. 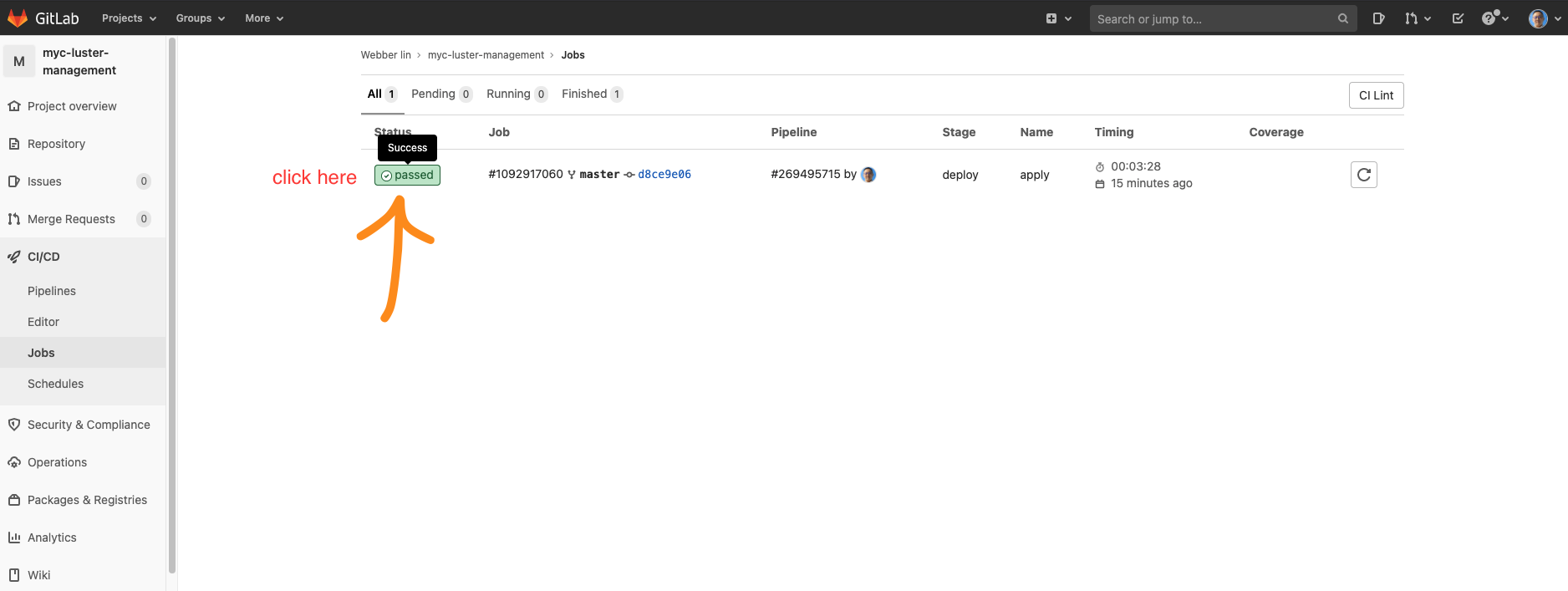 You will be redirected to the below page:
You will be redirected to the below page: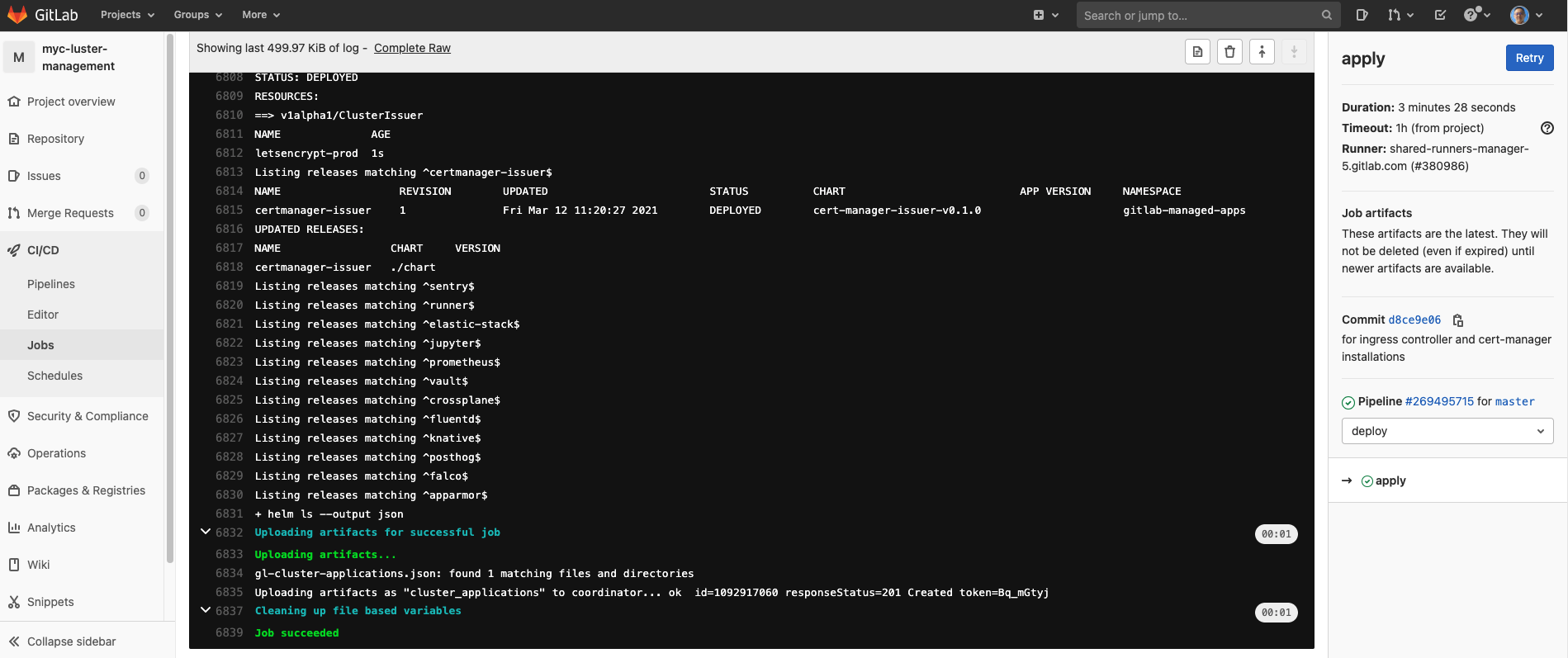
Verify your installation
From here, we need to use terminal to access your K8S cluster and determine the installations.
Using gcloud command to get GKE information
$ gcloud container clusters list
Once you know your cluster name and region, then type
$ gcloud container clusters get-credentials gitlab-demo-cluster --zone=asia-east1-c
OUTPUT:
Fetching cluster endpoint and auth data.
kubeconfig entry generated for gitlab-demo-cluster.
Using kubectl command to check ingress controller and cert-manager
For quick typing, we suggest you to use alias
$ alias k=kubectl
kubectl commands
check all deployments
$ k get deploy -n gitlab-managed-apps
check all pods
$ k get po -A
You can see the namespace GitLab used to create objects is "gitlab-managed-apps", so you can try
$ k get all -n gitlab-managed-apps
Cert-manager and ingress controller pods are all running, and service for ingress-controller is also up and running (with external IP). 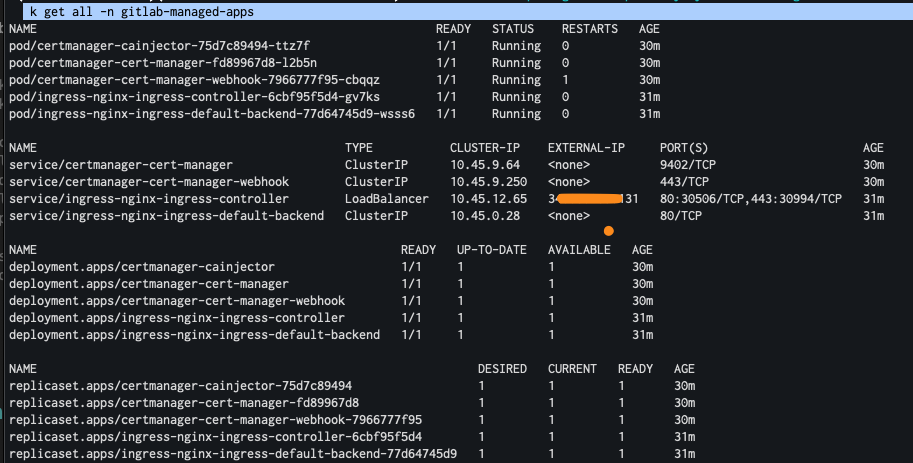
What's next?
In next demo, we will show you how to create a web service and assign a domain name to the service with TLS. We are going to use GitLab CI/CD to deploy Golang Application on K8S.


